Securing Communications of UAVs
About
Drones are fast becoming a popular consumer and commercial product. With the prominent use of drones throughout US military operations and subsequent security risks publicized by the media, this project aims to survey possible attack vectors of consumer grade unmanned air vehicles as well as, testing whether or not these vectors are, in fact, possible on a consumer grade drone.
Dr. Mohammad Husain
Joe Needleman
Ashly Barton
Project Details
Hardware
Parrot Drone AR 2.0
The drone we used to complete our experiments was the Parrot AR 2.0. In terms of total revenue, Parrot is the 2nd largest drone company. The retail price of it’s most popular model is roughly $400. Once the drone is powered on, it hosts its own wireless network automatically. The user must connect to this network via their supported (android or iOS) device in order to fly the drone. It is also necessary to install a mobile application maintained by Parrot. This application has a “piloting mode” that ultimately unables the user to launch and maneuver the drone.
Software
Wireless Network Cracking
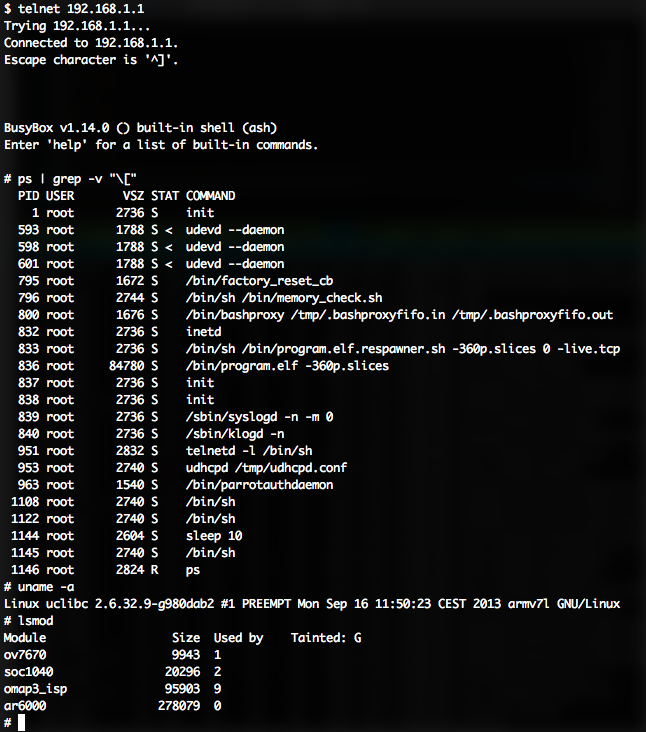
Once we got on the firmware the telnet interface was running as root, so we were able to reconfigure the firewall - and effectively disable it using iptables. With the firewall down, it did not reconfigure or lock its elf down when a client connected allowing multiple clients to connect to the drone causing confusion on which user should stay connected. This action caused the drone to drop out of the air several times in our tests.
Further research indicated it would be ideal to use the drone as an embedded platform to track and monitor networks. We were able to reconfigure the drone to act as a Wireless Client and a Wifi AP, so we could both connect to the drone and use the drone to connect elsewhere. By cross compiling WPASupplicant (used on all Linux systems to authenticate WPA2), we were able to get the drone to connect to normal networks. This also gives us ability to brute force wireless connections in the area - first listing it and then attempting common passwords and storing the results.
Further efforts are still underway to compile the full sets of tools statically. This would allow us to use the drone to sniff all local packets and log it to storage or exploit local devices. This in theory could be returned, and use the drone in a malicious manner which would upload infected binaries to client phone or networks it hijacks. Unlike previous research, this does not require additional payloads (Pi) and can be done on the drone itself without degradation of flight.
Eventually, we will be continuing our research by introducing an additional drone and mimicking drone-on-drone attack vectors.
Sponsors
This project would not be possible without the help of: